As part of this month’s Continuing Privacy and Security Training (“CPST”), The Compliance Team sought to explain “What is Phishing?”
Phishing is a type of cybersecurity attack during which malicious actors send messages pretending to be a trusted person or entity. Phishing messages manipulate a user, causing them to perform actions like installing a malicious file, clicking a malicious link, or divulging sensitive information such as access credentials. Phishing is the most common type of social engineering, which is a general term describing attempts to manipulate or trick computer users. Social engineering is an increasingly common threat vector used in almost all security incidents. Social engineering attacks, like phishing, are often combined with other threats, such as malware, code injection, and network attacks.
PHISHING ATTACKS: STATISTICS & EXAMPLES
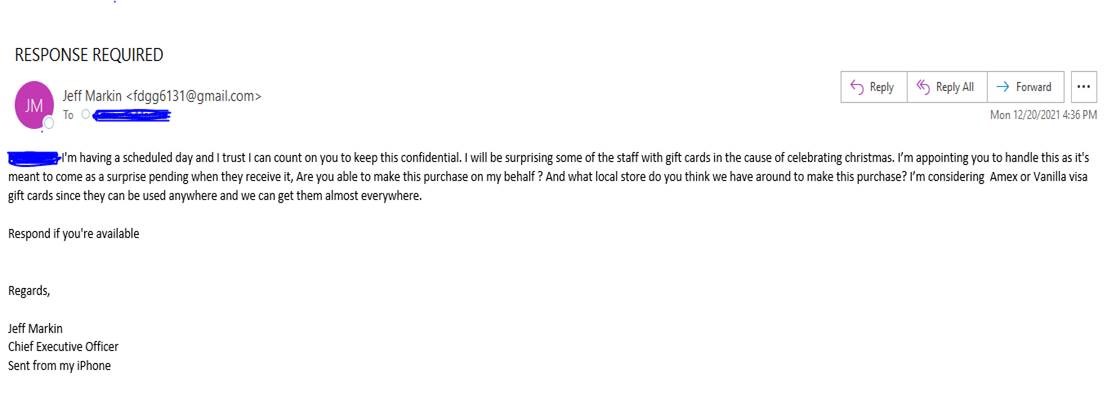
Message From CEO Scam
We all trust our CEO, especially when it comes to receiving highly important emails relating to company-wide updates. The problem is, cyber criminals know just how much trust we place in our Executives.
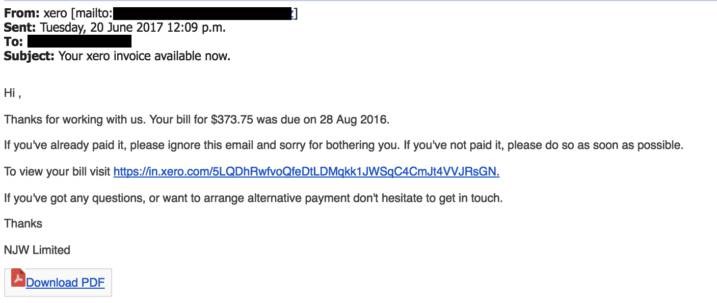
The Fake Invoice Scam
The arguably the most popular phishing template out there – the fake invoice technique. Like many phishing attacks, this scam relies on fear and urgency, pressuring an end user to submit a payment for goods or services they’ve never even ordered or received.
Email Account Upgrade Scam
Faced with having your account expire unless immediate action is taken, the email account upgrade scam can appear to come from trusted email providers like Microsoft and Google, or simply from our company’s IT department.

How Phishing Works
The basic element of a phishing attack is a message, sent by email, social media, or other electronic communication means.
A phisher may use public resources, especially social networks, to collect background information about the personal and work experience of their victim. These sources are used to gather information such as the potential victim’s name, job title, and email address, as well as interests and activities. The phisher can then use this information to create a reliable fake message.
Typically, the emails the victim receives appear to come from a known contact or organization. Attacks are carried out through malicious attachments or links to malicious websites. Attackers often set up fake websites, which appear to be owned by a trusted entity like the victim’s bank or workplace. Via these websites, attackers attempt to collect private information like usernames and passwords, or payment information.
Some phishing emails can be identified due to poor copywriting and improper use of fonts, logos, and layouts. However, many cybercriminals are becoming more sophisticated at creating authentic-looking messages, and are using professional marketing techniques to test and improve the effectiveness of their emails.
TYPES OF PHISHING ATTACKS
Email Phishing
Most phishing attacks are sent via email. Attackers typically register fake domain names that mimic real organizations and send thousands of common requests to victims.
Many phishing emails use a sense of urgency, or a threat, to cause a user to comply quickly without checking the source or authenticity of the email.
Email phishing messages have one of the following goals:
- Causing the user to click a link to a malicious website, in order to install malware on their device.
- Causing the user to download an infected file and using it to deploy malware
- Causing the user to click a link to a fake website and submit personal data.
- Causing the user to reply and provide personal data.
Spear Phishing
Spear phishing includes malicious emails sent to specific people. The attacker typically already has some or all of the following information about the victim:
- Name
- Place of employment
- Job title
- Email address
- Specific information about their job role
- Trusted colleagues, family members, or other contacts, and samples of their writing
This information helps increase the effectiveness of phishing emails and manipulate victims into performing tasks and activities, such as transferring money.
Smishing and Vishing
This is a phishing attack that uses a phone instead of written communication. Smishing involves sending fraudulent SMS messages, while vishing involves phone conversations.
In a typical voice phishing scam, an attacker pretends to be a scam investigator for a credit card company or bank, informing victims that their account has been breached. Criminals then ask the victim to provide payment card information, supposedly to verify their identity or transfer money to a secure account (which is really the attacker’s).
Vishing scams may also involve automated phone calls pretending to be from a trusted entity, asking the victim to type personal details using their phone keypad.
WHAT ARE THE SIGNS OF PHISHING?
Threats or a Sense of Urgency
Emails that threaten negative consequences should always be treated with skepticism. Another strategy is to use urgency to encourage or demand immediate action. Phishers hope that by reading the email in a hurry, they will not thoroughly scrutinize the content and will not discover inconsistencies.
Message Style
An immediate indication of phishing is that a message is written with inappropriate language or tone. If, for example, a colleague from work sounds overly casual, or a close friend uses formal language, this should trigger suspicion. Recipients of the message should check for anything else that could indicate a phishing message.
Unusual Requests
If an email requires you to perform non-standard actions, it could indicate that the email is malicious. For example, if an email claims to be from a specific IT team and asks for software to be installed, but these activities are usually handled centrally by the IT department, the email is probably malicious.
Linguistic Errors
Misspellings and grammatical misuse are another sign of phishing emails. Most companies have set up spell checking in their email clients for outgoing emails. Therefore, emails with spelling or grammatical errors should raise suspicion, as they may not originate from the claimed source.
Inconsistencies in Web Addresses
Another easy way to identify potential phishing attacks is to look for mismatched email addresses, links, and domain names. For example, it’s a good idea to check a previous communication that matches the sender’s email address.
Recipients should always hover over a link in an email before clicking it, to see the actual link destination. If the email is believed to be sent by Bank of America, but the domain of the email address does not contain “bankofamerica.com”, that is a sign of a phishing email.
Request for Credentials, Payment Information or Other Personal Details
In many phishing emails, attackers create fake login pages linked from emails that appear to be official. The fake login page typically has a login box or a request for financial account information. If the email is unexpected, the recipient should not enter login credentials or click the link. As a precaution, recipients should directly visit the website they think is the source of the email.
WAYS TO PREVENT PHISHING ATTACKS
- Always be suspicious of password reset emails
Password reset emails are designed to help when you can’t recall the password for your account. By clicking on a link, you can reset the password to that account to something new. Not knowing your password is, of course, also the problem that cybercriminals face when trying to gain access to your online accounts. By sending a fake password reset email that directs you to a lookalike phishing site, they can convince you to type in your account credentials and send those to them. If you receive an unsolicited password reset email, always visit the website directly (don’t click on embedded links) and change your password to something different on that site (and any other sites with the same password).
- Always note the language in the email
Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority.
Fake Order/Delivery: A phishing email will impersonate a trusted brand (Amazon, FedEx, etc.) stating that you have made an order or have an incoming delivery. When you click to cancel the unauthorized order or delivery, the website (which belongs to a cybercriminal) will require authentication, enabling the attacker to steal login credentials.
Business Email Compromise (BEC): BEC scams take advantage of hierarchy and authority within a company. An attacker will impersonate the CEO or other high-level executive and order the recipient of the email to take some action, such as sending money to a certain bank account (that belongs to the scammer).
Fake Invoice: The phisher will pretend to be a legitimate vendor requesting payment of an outstanding invoice. The end goal of this scam is to have money transferred to the attacker’s account or to deliver malware via a malicious document.
In other words, if an email is urging you to take rapid or unusual actions, slow down and verify that it is legitimate before trusting it. Additionally, it is important to consider whether a phishing email’s tone is “on brand” for the supposed sender. Phishing emails will often – but not always – contain misspellings, grammatical errors, or unusual phrasing. If an email doesn’t “sound right”, then don’t trust it.
- Never share your credentials
Credential theft is a common goal of cyberattacks. Many people reuse the same usernames and passwords across many different accounts, so stealing the credentials for a single account is likely to give an attacker access to a number of the user’s online accounts.
As a result, phishing attacks are designed to steal login credentials in various ways, such as:
Phishing Sites: Attackers will create lookalike sites that require user authentication and point to these sites in their phishing emails. Beware of links that don’t go where you expect them to.
Credential-Stealing Malware: Not all attacks against your credentials are direct. Some phishing emails carry malware, such as keyloggers or trojans, that are designed to eavesdrop when you type passwords into your computer.
Support Scams: Cybercriminals may pose as customer support specialists from Microsoft, Apple, and similar companies and ask for your login credentials while they “help” you with your computer.
Cybercriminals use a lot of different pretexts and scams to attempt to steal your account credentials. Never tell anyone your password, and, if an email points to a login page, visit the site directly and authenticate from there to protect against lookalike phishing sites.
As always, please let the eHealth Technologies’ Privacy and Security Compliance Team know if you have any questions on the privacy and security of Covered Information, including PHI, ePHI, and other Confidential Information.