Good day to all Global Team Members.
As part of this month’s Continuing Privacy and Security Training (“CPST”), The Compliance Team sought to explain ” What is Social Engineering Attacks and its Prevention!!!”.
The IT Security Team has observed an increase in social engineering attacks targeting eHealth employees. Please read this CPST fully to see some examples of the attacks that are targeting us.
What is social engineering?
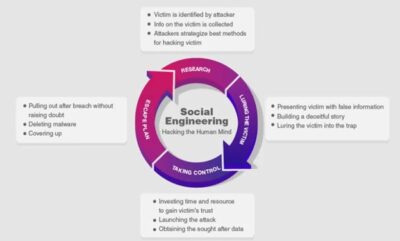
Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into making security mistakes or giving away credentials, banking details, or other sensitive information.
Social engineering attacks happen in one or more steps. A attacker first investigates the intended victim to gather necessary background information, such as potential points of entry and weak security protocols, needed to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide stimuli for subsequent actions that break security practices, such as revealing sensitive information or granting access to critical resources.
Social engineering attack techniques:
The following five techniques are among the most commonly used social engineering attacks.
- Phishing
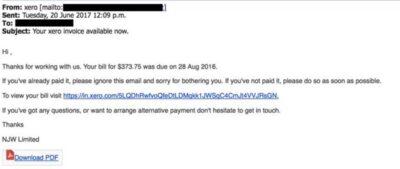
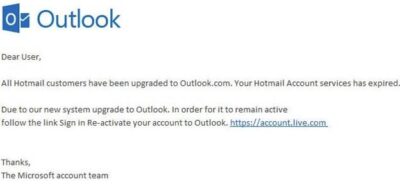
In a phishing attack, an attacker uses a message sent by email, social media, instant messaging clients or SMS to obtain sensitive information from a victim or trick them into clicking a link to a malicious website.
Phishing messages get a victim’s attention and call to action by arousing curiosity, asking for help, or pulling other emotional triggers. They often use logos, images or text styles to spoof an organization’s identity, making it seem that the message originates from a work colleague, the victim’s bank, or other official channel. Most phishing messages use a sense of urgency, causing the victim to believe there will be negative consequences if they don’t surrender sensitive information quickly.
- Watering hole
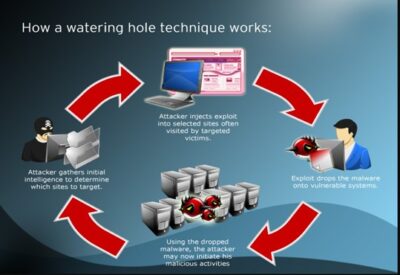
A watering hole attack involves launching or downloading malicious code from a legitimate website, which is commonly visited by the targets of the attack. For example, attackers might compromise a financial industry news site, knowing that individuals who work in finance and thus represent an attractive target, are likely to visit this site.
Watering hole attacks are usually performed by skilled attackers who have discovered a zero-day exploit. They might wait for months before performing the actual attack to preserve the value of the exploit they discovered. In some cases, watering hole attacks are launched directly against vulnerable software used by the target audience, rather than a website they visit.
- Whaling attack
Whaling, also known as spear phishing, is a type of phishing attack that targets specific individuals with privileged access to systems or access to highly valuable sensitive information. For example, a whaling attack may be conducted against senior executives, wealthy individuals, or network administrators.
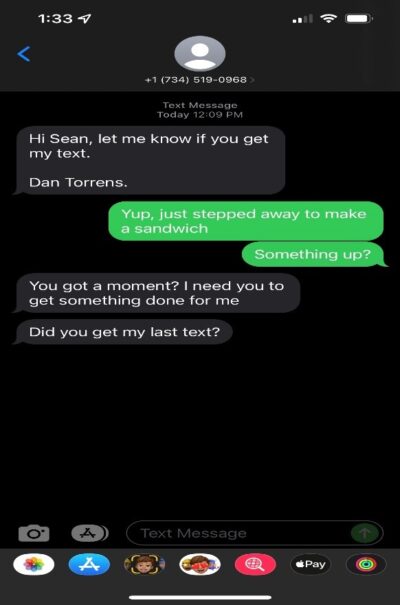
Here is an example of a real attack recently targeting one of our employees:
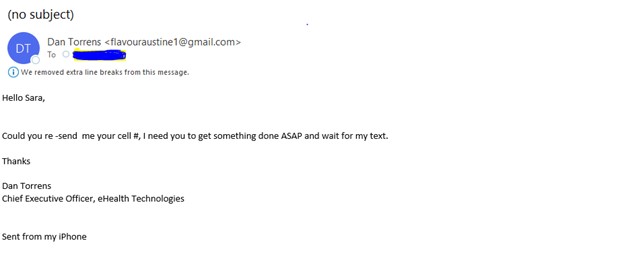
4. Pretexting
Pretexting is a type of social engineering technique where the attacker creates a scenario where the victim feels compelled to comply under false pretenses. Typically, the attacker will impersonate someone in a powerful position to persuade the victim to follow their orders.
During this type of social engineering attack, a bad actor may impersonate police officers, higher-ups within the company, auditors, investigators or any other persona they believe will help them get the information they seek.
Here is yet another example of a real attack recently targeting one of our employees:
- Baiting and quid pro quo attacks
In a baiting attack, attackers provide something that victims believe to be useful. This may be a supposed software update which in fact is a malicious file, an infected USB token with a label indicating it contains valuable information and other methods.
A quid pro quo attack is similar to baiting, but instead of promising something that will provide value to the victim, the attackers promise to perform an action that will benefit them, but requires an action from the victim in exchange. For example, an attacker may call random extensions at a company, pretending to be calling back on a technical support inquiry. When they identify an individual who actually has a support issue, they pretend to help them, but instruct them to perform actions that will compromise their machine.
Social engineering prevention:
Social engineers manipulate human feelings, such as curiosity or fear, to carry out schemes and draw victims into their traps. Therefore, be wary whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across stray digital media lying about. Being alert can help you protect yourself against most social engineering attacks taking place in the digital realm.
Moreover, the following tips can help improve your vigilance in relation to social engineering hacks.
- Don’t open emails and attachments from suspicious sources – If you don’t know the sender in question, you don’t need to answer an email. Even if you do know them and are suspicious about their message, cross-check and confirm the news from other sources, such as via telephone or directly from a service provider’s site. Remember that email addresses are spoofed all of the time; even an email purportedly coming from a trusted source may have actually been initiated by an attacker.
- Use multifactor authentication – One of the most valuable pieces of information attackers seek are user credentials. Using multifactor authentication helps ensure your account’s protection in the event of system compromise.
- Be wary of tempting offers – If an offer sounds too enticing, think twice before accepting it as fact. Googling the topic can help you quickly determine whether you’re dealing with a legitimate offer or a trap.
- Keep your antivirus/antimalware software updated – Make sure automatic updates are engaged, or make it a habit to download the latest signatures first thing each day. Periodically check to make sure that the updates have been applied, and scan your system for possible infections.
As always, please let the eHealth Technologies’ Privacy and Security Compliance Team know if you have any questions on the privacy and security of Covered Information, including PHI, ePHI, and other Confidential Information.
Thank you for Caring Together…
eHT Compliance Team